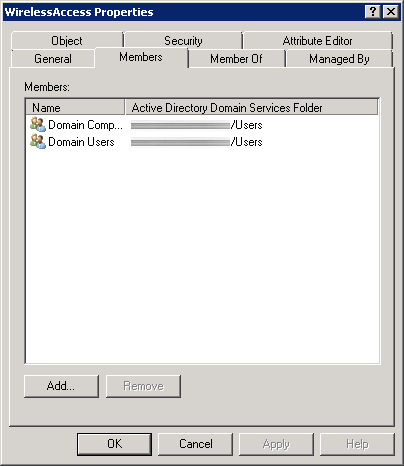
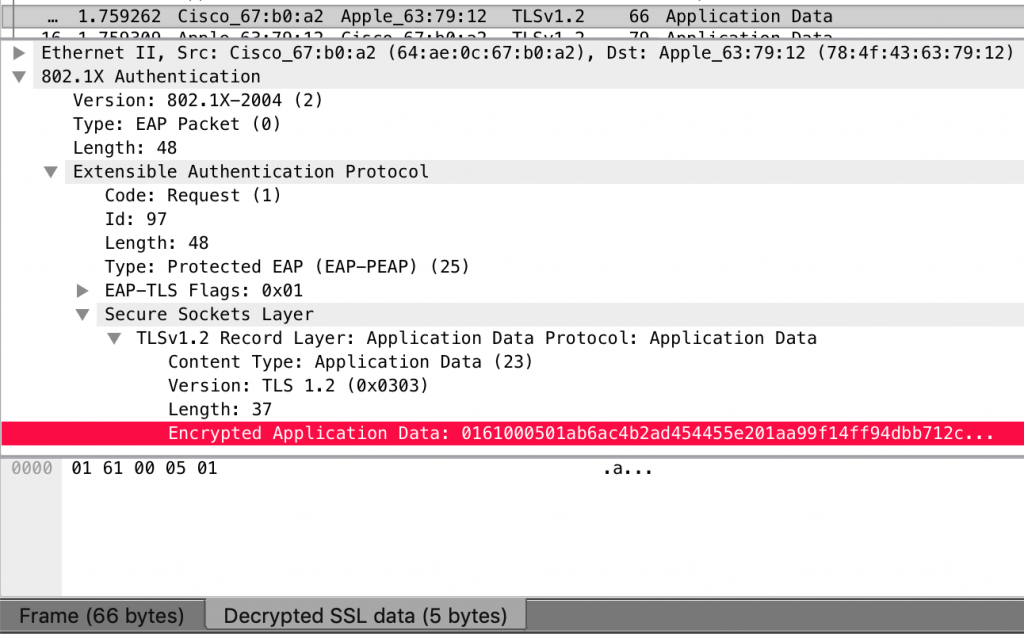
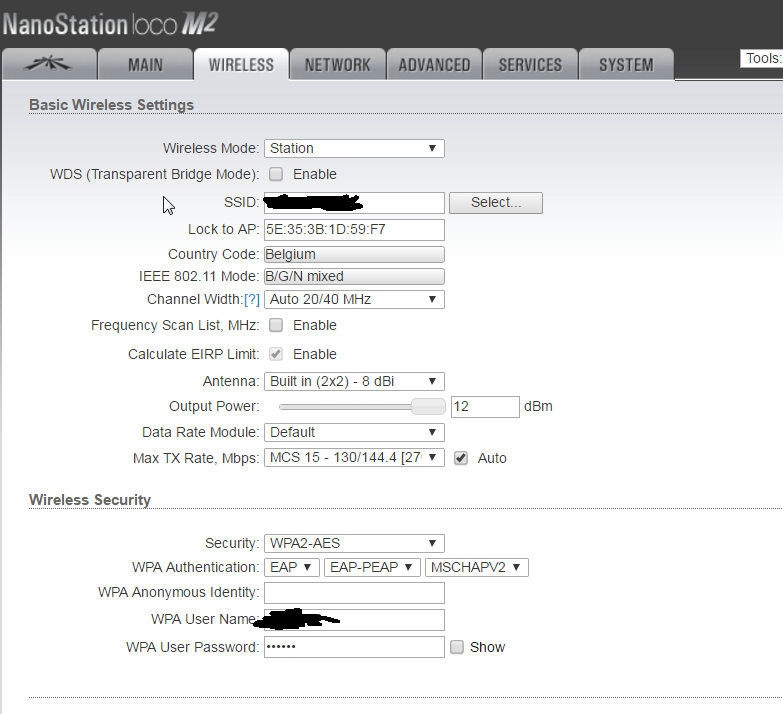
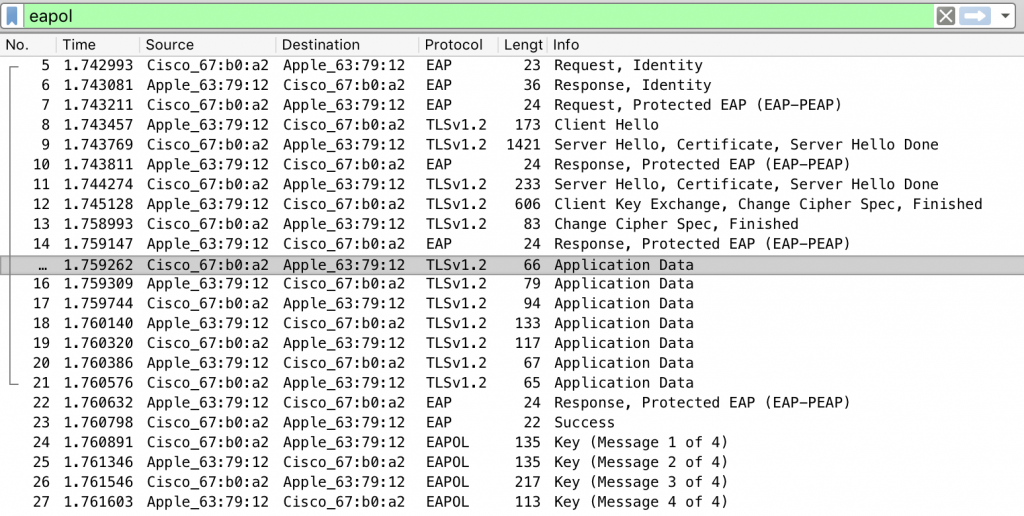
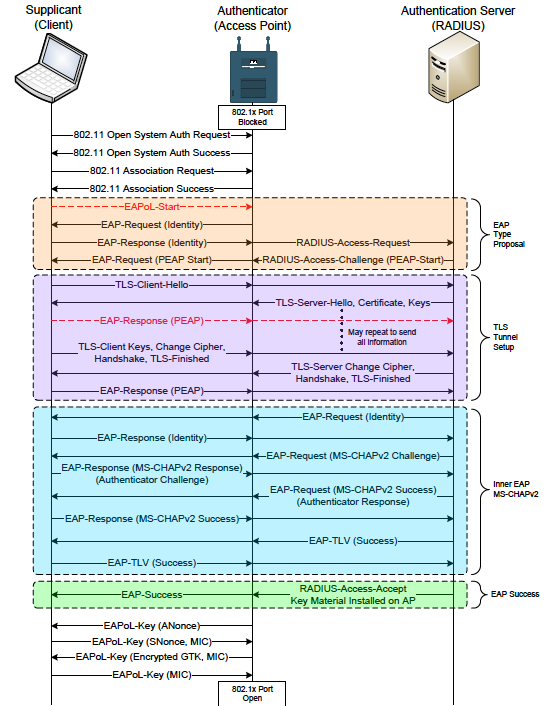
Whitepaper: Bypassing Port Security In 2018 – Defeating MACsec and 802.1x-2010 DEF CON 26 Gabriel Ryan (@s0lst1c3) August 2018
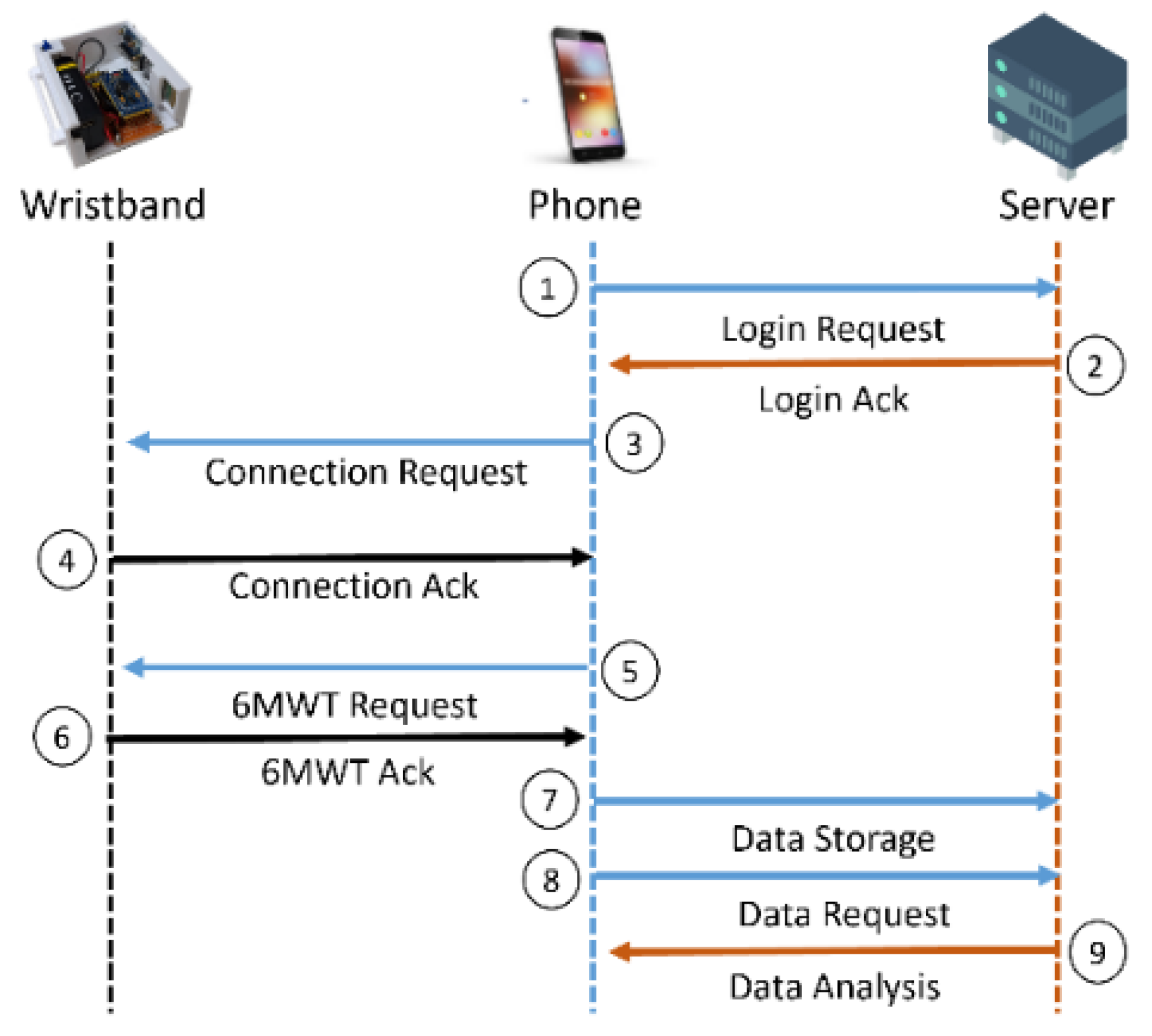
Biosensors | Free Full-Text | A Pervasive Pulmonary Function Estimation System with Six-Minute Walking Test
UNIVERSITY OF CASTILLA-LA MANCHA UNIVERSITY COLLEGE OF COMPUTER SCIENCE INFORMATION SECURITY AND CYBERSECURITY MASTER'S DEGREE

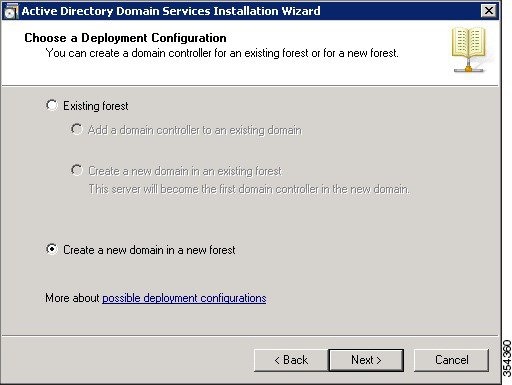
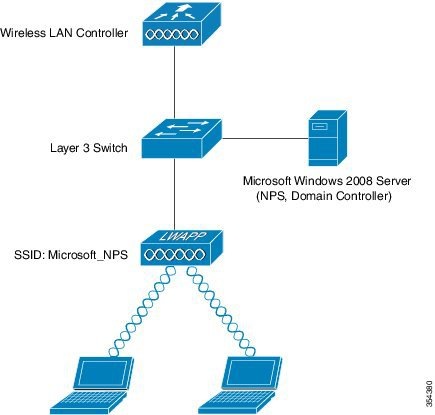
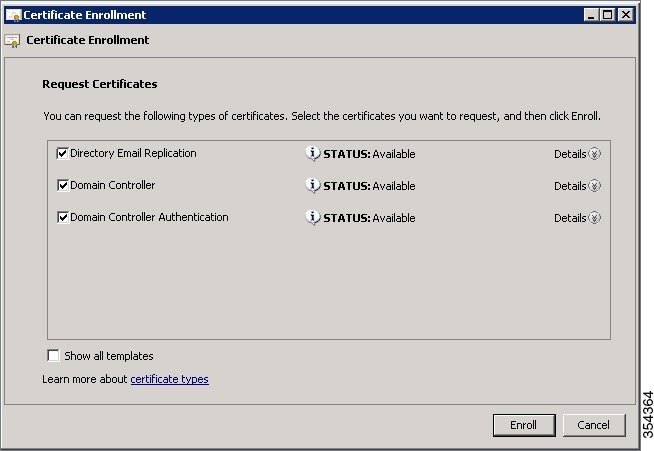
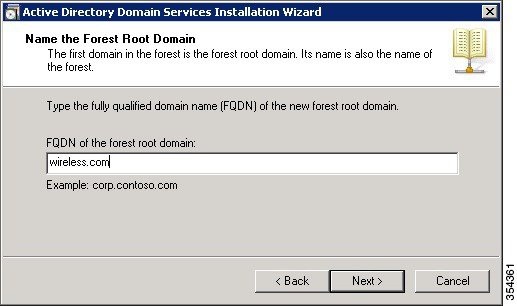
Addressing the WLAN Security Challenges > Cisco Unified Wireless LAN Security Fundamentals | Cisco Press